 Introductory Comments On Voting Problems by Charles E. Corry, Ph.D.
Introductory Comments On Voting Problems by Charles E. Corry, Ph.D. Introductory Comments On Voting Problems by Charles E. Corry, Ph.D.
Introductory Comments On Voting Problems by Charles E. Corry, Ph.D.| EJF Home | Where To Find Help | Join the EJF | Comments? | Get EJF newsletter |
| Vote Fraud and Election Issues Book | Table of Contents | Site Map | Index |
| Chapter 1 — Introduction To Voting Problems |
| Next — Former Election Assistance Commission Chair States There Are No Standards And System Ripe For Stealing An Election |
Survey: Firms mum on hacker attacks — FBI seeks to ease fears on reporting
Where are the protections against hacking computer voting systems?
Election officials and voting system vendors
Thomas Paine wrote over 200 years ago: "The right of voting for representatives is the primary right by which all other rights are protected. To take away this right is to reduce a man to slavery."
Or the still ringing words of Dr. Martin Luther King from a speech delivered before the Lincoln Memorial at the March on Washington on May 17, 1957, eight years before the enactment of the Voting Rights Act.
"Three years ago the Supreme Court of this nation rendered in simple, eloquent and unequivocal language a decision which will long be stenciled on the mental sheets of succeeding generations. For all men of good will, this May 17 decision came as a joyous daybreak to end the long night of segregation. It came as a great beacon light of hope to millions of distinguished people throughout the world who had dared only to dream of freedom. It came as a legal and sociological deathblow to the old Plessy doctrine of "separate-but-equal." It came as a reaffirmation of the good old American doctrine of freedom and equality for all people.
Unfortunately, this noble and sublime decision has not gone without opposition. This opposition has often risen to ominous proportions. Many states have risen up in open defiance. The legislative halls of the South ring loud with such words as "interposition" and "nullification." Methods of defiance range from crippling economic reprisals to the tragic reign of violence and terror. All of these forces have conjoined to make for massive resistance.
But, even more, all types of conniving methods are still being used to prevent Negroes from becoming registered voters. The denial of this sacred right is a tragic betrayal of the highest mandates of our democratic traditions and its is democracy turned upside down.
So long as I do not firmly and irrevocably possess the right to vote I do not possess myself. I cannot make up my mind - it is made up for me. I cannot live as a democratic citizen, observing the laws I have helped to enact - I can only submit to the edict of others.
So our most urgent request to the President of the United States and every member of Congress is to give us the right to vote. Give us the ballot and we will no longer have to worry the federal government about our basic rights. Give us the ballot and we will no longer plead to the federal government for passage of an anti-lynching law; we will by the power of our vote write the law on the statute books of the southern states and bring an end to the dastardly acts of the hooded perpetrators of violence. Give us the ballot and we will transform the salient misdeeds of blood-thirsty mobs into calculated good deeds of orderly citizens. Give us the ballot and we will fill our legislative halls with men of good will, and send to the sacred halls of Congressmen who will not sign a Southern Manifesto, because of their devotion to the manifesto of justice. Give us the ballot and we will place judges on the benches of the South who will "do justly and love mercy," and we will place at the head of the southern states governors who have felt not only the tang of the human, but the glow of the divine. Give us the ballot and we will quietly and nonviolently, without rancor or bitterness, implement the Supreme Court's decision of May 17, 1954."
It is our belief that there is nothing more fundamental to the preservation of our republic than fair, open, and honest elections utilizing a secret ballot with one, and only one vote for each eligible citizen. However, it is historical fact that election fraud has existed since the inception of our country, and those motivated by malice and greed can be expected to continue their attempts to rig elections into the forseeable future. The basic techniques are outlined in the Chicago Rules Of Election Fraud. Or see a demonstration of how a computer can control an election at WheresThePaper. In the test election there you get honest results but Mary Smith always wins in the "real" election no matter how many votes you give John Doe.
Of course, if you want to play with real election software you can learn how to rig or edit any election here that uses Diebold voting equipment. You'll need to download and install the Diebold vote-tally software and you'll need Microsoft Access, which comes with Microsoft Office. Most any teenager can do this.
It should never be forgotten that murder and intimidation have always been a part of American elections. Some examples:
• In April 2002 a candidate for sheriff in Pulaski County, Kentucky, killed the incumbent, his political opponent, before the election.
• In 2000, a man Tennessee prosecutors said was consumed by a thirst for political power was sentenced to life in prison for the 1998 shooting death of his election opponent, a state senator.
• In Georgia, former DeKalb County Sheriff Sidney Dorsey ordered the murder of the man who defeated him for re-election in December 2000. Four men carried out the murder on Dorsey's orders. Dorsey and two of the killers were convicted of murder and given life in prison. Two of the four were granted immunity from prosecution for turning state's witness.
However, one need not propose homicide or a massive conspiracy to rig an election in order to suggest that all reasonable precautions must be taken to protect the integrity of our elections. Most of the precautions and procedures one finds in elections today were put in place as a result of hard-won experience with fraud and intimidation. After all, the classical dirty political machines, e.g., Tammany Hall in New York, Daley in Chicago, LBJ in Texas, gained, or remained in power by relying on the local ward bosses to somehow stuff the ballot box as needed. It would be foolish in the extreme to suggest that simply switching to computer voting will automatically eliminate, or even reduce such election fraud. In fact, all the evidence suggests that computer voting will make election fraud possible with an ease and scale heretofore impossible to achieve.
But the idea that a well funded adversary, such as the intelligence service of a foreign government, would be interested in tampering with the results of a U.S. election should not be lightly dismissed. Such an effort would be cheaper than the rent on the Lincoln Bedroom in the White House and more sure of a "positive" result than the $500,000 the Chinese are reported to have donated to the Clinton campaign.
Since the problems of the presidential election of 2000 there has been an accelerating movement towards the use of computers in elections for a multitude of functions including voter registration, ballot generation, ballot counting, transmittal of election results, and etc. That movement has been fueled by the Help America Vote Act of 2002, or HAVA, that authorized $3.9 billion to be spent over three years to help state and local governments upgrade their election equipment. These billions of dollars left voting machine manufacturers slobbering at the public trough with little regard to the future of our democracy.
In working with IEEE to establish national standards for voting equipment I have also been struck by the lack of any cost-benefit analysis for these systems. Present Direct Recording Electronic (DRE) voting machines are little more than very expensive toys. As that has become ever more apparent, there has been a growing national demand that these toys print out a paper backup that voters can verify and canvass boards and poll watchers can audit. What benefit is there then to placing very expensive DREs with ballot printers (~$4,000 each with a design life of twenty elections), and say a minimum of five DREs per precinct, to replace paper ballots? Further, paper ballots are still needed for absentee and provisional voters.
Other than some possible convenience for county clerks, I have yet to see any advantage to thousands of very expensive ballot printers located in every precinct over centrally printing paper ballots and distributing those paper ballots to the precincts. And paper ballots require very little in the way of technical and computer expertise, commodities woefully short in most county clerk's offices.
Further, a Caltech/MIT study undertaken after the contentious presidential election in 2000 found that hand-counting paper ballots was the most accurate of the four methods (hand counting, optical scan, DRE, punch card) evaluated. DREs were among the least accurate.
It is also quite clear that the classical Congressional approach of throwing money at a problem under the Help America Vote Act of 2002 (HAVA) was completely backwards from the methods that should have been used when the issue is as basic to our democracy as voting. Under HAVA $3.9 billion was allocated to purchase voting equipment but virtually nothing was appropriated for research, testing, and development. Thus, instead of a period of testing equipment and developing standards prior to deployment, election officials have now spent billions on electronic voting equipment for which no standards exist and which have undergone only fragmentary testing. As a result both the manufacturers and election officials are extremely defensive about their actions and products, which clearly lack the features and security the evolving standards will require.
Also, what has been swept under the carpet is the fact that the traditional functions of poll watchers and citizen election judges in monitoring ballot counting have been completely eliminated with electronic voting. Voters touch a screen and everyone "trusts" the machine does the count accurately or, at best, the voter feeds a ballot into a black box and "trusts" the machine to count accurately. However, in practice there is virtually no way for election judges or poll watchers to verify the numbers produced by computer voting machines.
In addition, the amount, and cost, of training and expertise demanded of local election officials to competently run electronic elections has been totally neglected. Nor has there been any evaluation of the costs for maintenance, upgrades, programming, climate-controlled storage, and other hidden expenses of computer voting. From my perspective it would seem that a cost-benefit analysis of electronic elections is still required and quite likely to show computer voting is not an effective or safe method.
Voting by computers is based on the premise that the average county clerk can maintain a computer system and network that is more secure and error-free than anything the United States Department of Defense has been able to establish. And those who know the least about computers appear to be most in favor of their use in elections, i.e., if you don't know a bit from a byte, or a gate from a flip-flop, then the government will give you billions to buy voting computers. Realistically, most county and parrish clerks are as familiar with computers as they are with handling nitroglycerin and it is probably safer to give them the nitro as they are likely to be more careful with it.
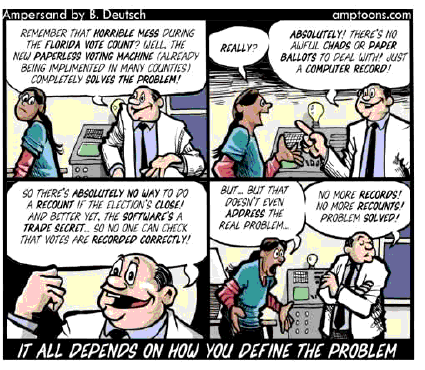
As the premise that county clerks are generally aware of, and capable of providing secure computer facilities is obviously fallacious, wondrous new opportunities have been opened up for the mass rigging of elections. Computer technology provides numerous opportunities that were previously forestalled simply by the logistics of handling and counting paper ballots at individual precincts. It is as though we are not only giving these clerks nitroglycerin, we have partially frozen it first.
There is also a correlation between election districts that are rushing into computer voting and voting irregularities. At present it is unknown whether the election problems are associated with the voting machines or the election officials. Of course, in these times, the blame will be placed on the computers and technicians as it would be unthinkable for incompetence in a public official to be admitted.
It is also our experience that when vendors of computer voting equipment, e.g.,
Diebold,
are queried they have two standard responses: (a) the enquiry must be from someone who is technologically ignorant, or (b) if the technical qualifications of the enquirer are unquestionable they are met with silence or outright rejection.

On August 14, 2003, Diebold CEO Walden O'Dell told Republicans in a fund-raising letter that he is "committed to helping Ohio deliver its electoral votes to the president next year." That prompted Ohio Democrats, among others, to question the propriety of allowing O' Dell's company to calculate votes in the 2004 presidential election as well as a clever satire of Diebold Election Systems. In the event, however, despite numerous irregularities, Ohio did vote for Bush. That "vote" was helped considerably by the fact that Ohio's Secretary of State at the time was also Bush's campaign manager. The "irregularities" would eventually find several election officials in Cuyahoga County, Ohio's most populous, convicted of election fraud, but the election results would stand, as they almost always do even when fraud is proven.
We have also noted that state and county committees that select computer voting equipment rarely encourage input from technically-qualified individuals, who may be dismissed as paranoid. Take for example the following experience of Dr. Rebecca Mercuri at the 2003 IACREOT convention in Denver:
Reproduced under the Fair Use exception of 17 USC § 107 for noncommercial, nonprofit, and educational use.
Denver Post, Sunday, August 3, 2003 — A prominent critic of electronic voting was booted out of last week's conference of the International Association of Clerks, Recorders, Election Officials and Treasurers in Denver.
"It seems the nation's election officials aren't open to input from anyone but the industries that are wining and dining them to buy their equipment," said Rebecca Mercuri, a computer science professor at Bryn Mawr College [See A Better Ballot Box? ].
Mercuri on Thursday was asked to leave the conference at Denver's Adam's Mark Hotel after she and several other computer scientists raised questions earlier in the week about technological vulnerabilities with voting equipment that could lead to election tampering and fraud.
Group officials said she did not belong at the meeting because she is not a public official.
"She was not qualified to be a registered delegate," said Stanley Kusper, general counsel for the association.
Incidentally, for the web savvy, below is the complete HTML source code for the home page of the IACREOT site as of August 4, 2003:
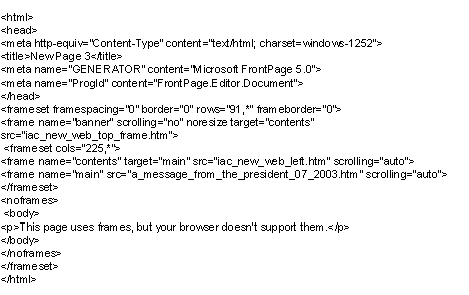
If IACREOT has upgraded their site since August of 2003 you can use the Way Back Machine to locate www.iacreot.com for the date nearest August 4, 2003.
Anyone with more than ten minutes experience using HTML, or designing a web site will recognize this as an ideal candidate for Web Pages That Suck. In our opinion a national organization that lacks even a title, let alone metatags in its homepage lacks any understanding of computers beyond where the "On" switch is located. It is frightening to realize that IACREOT is the primary organization for our election officials.
Our experience with computer hacking is that people tend to ignore it until it happens to them. Once someone has their system or account hacked they believe you can't be paranoid enough about it. But how common is computer hacking? Consider the following story from the business section of the Denver Post:
by Jennifer Beauprez, Denver Post Business Writer
Reproduced under the Fair Use exception of 17 USC § 107 for noncommercial, nonprofit, and educational use.
Monday, August 4, 2003 — As many as half of all businesses suffered break-ins from hackers last year, [emphasis added] but most didn't say a peep about it to law enforcement, a recent government report shows.
Only one-third of 530 companies surveyed by the Computer Security Institute said they reported hacking attacks to law enforcement. CSI interviews companies about security issues each year.
"We know we' re not getting all the phone calls," said Dave Mahon, FBI agent in charge of the computer-crimes division in Denver. "We know there's a lot more going on than is being reported."
Last year, the FBI created the 11-person computer-crimes squad in Denver to pursue computer intrusions, cyber-terrorism, child pornography, white-collar fraud and other Internet crimes.
The FBI Denver operation also started InfraGard, a club in which business members and the FBI share information online about computer crimes and hacking, and meet regularly to discuss security issues. The group, started in Denver two years ago, has 150 businesses as members.
Still, as many as 70 percent of businesses surveyed say they don't report computer intrusions to the FBI because they don't want the negative publicity, the report shows.
"They' re worried about the bottom line, and the CEO says 'Is this going to have a negative effect on my company?'" Mahon said. "Just because the FBI shows up, your name is not going to get in the paper as a victim. Preventing the next terrorist attack is more important than prosecuting."
Sometimes attacks that seem irrelevant individually may add up to be something more significant, Mahon said. For instance, a criminal who breaks into a computer to steal credit-card numbers or personal information could actually be selling that information to a terrorist, who uses a fake identity or to buy plane tickets. Or the hacking incident could be a warm-up for a bigger, more serious attack on our nation's power or water systems, he said.
"Almost every violent crime has a sort of computer nexus," Mahon said.
Many people don't realize, too, that it's a federal crime for an employee to break into computer systems beyond their authorization, Mahon said.
Most of the computer attacks — some 86 percent — came from disgruntled employees, the survey showed, up from 76 percent two years ago.
Companies also estimate they lost some $70.1 million worth of proprietary information last year via computer break-ins, and suffered $10.1 million in financial fraud as well.
Businesses who want to report hacking to the FBI can call 303-629-7171 and ask for the computer-crimes squad.
An eleven-man team of FBI agents in Denver alone to deal with computer hacking is a huge investment and well illustrates the magnitude of the prevalence and dangers of computer hacking to businesses. Similarly, the Department of Defense, and other federal agencies, invest hugely in defending against cyber attacks.
But when it comes to the defense of computer voting against hacking there are no federal agents to safeguard the systems. What is found is that independent investigators, regardless of credentials and experience, are treated as enemies by election officials and barred from even attending meetings, as in the case of Dr. Mercuri described above.
Instead we get statements that public officials dismiss warnings about computer and network security in voting systems as paranoid conspiracy theories. For example, "It's fear-mongering by a few people who want to go back to the 19th century-way of voting," Adams County Clerk and Recorder Carol Snyder said in a front-page article in the July 30, 2003, edition of the Denver Post. But one might also consider the workings of the nearby Arapahoe County Clerk, who the Denver Post labeled as a Doofus Too Dumb To Quit. Now if you happen to be looking for a couple of large Colorado counties to control the vote in, Adams and Arapahoe would seem to be great places to go. Carol Snyder has her head in the sand and Terry Baker has his other head in Lisa. And as of early 2005 worms, Trojan horses, viruses, hack tools, and other malicious code has become so pervasive on Microsoft Windows systems that it must be assumed that every machine using a Microsoft operating system is infected.
One of the primary uses of computers in elections are for databases containing election information. Whether for voter registration information, candidate data, or simply geographical information about voting districts, computers are ideally suited to handling such information.
Yet once again we find the Help America Vote Act of 2002 pushing elections on to untrodden ground with no thought of quicksand. For example, voter registration databases are now to become statewide and, one suspects, eventually national. We shall put aside for the moment grave concerns about national identity cards, or even statewide cards, and look simply at the security concerns.
In the 2002 election in Florida, Governor Jeb Bush, a Republican, and his Secretary of State, Katherine Harris, ordered all convicted felons to be purged from the voter registration roles statewide. In the event some 91,000 individuals were removed from the voting rolls, only about 5,000 of whom actually had a felony conviction. The remainder proved to be largely black Democrats or citizens with similar names to felons. After the gubernatorial election, where Jeb Bush was reelected, and Katherine Harris won a congressional seat, county clerks were ordered to correct the "mistakes." Other potential uses for disenfranchising voters one doesn't like are simply increased when the pollbook is kept on a statewide basis. For example, among other tricks that would become easily possible, at noon on election day a hacker might simply mark selected voters, e.g., female Democrats over age 50, as having already voted and thus ineligible to vote again when they show up at the polls.
With HAVA and statewide voter registration databases the linkage is supposed to be through the Internet. Does it need to be repeated that every known network has been hacked at some point? Having worked with relational databases since 1978, virtually since their invention, I can say with authority that database security is no better than the database administrators (DBA's) in charge of the system. Having worked with about 100 DBA's I found about 10 of them capable of setting up even a quasi-secure database. And none of those would want to guarantee the security of an Internet-linked database. So what is HAVA pushing to do but set up statewide databases linked through the Internet.
The purported purpose of a statewide voter registration database is that it will prevent citizens from registering to vote in more than one jurisdiction. As any competent DBA will tell you, names are one of the worst nightmares in designing and maintaining a database. Easy you say, just use a unique identifier, like their Social Security number, as a unique key. Now stop and think for a second, just how many illegal immigrants are there in Colorado, or California. And what do illegals need to get a job? A Social Security number. Now how many of the numbers used by these illegal immigrants duplicate valid numbers of citizens? Names, birthdates, mother's maiden name, etc., are all used to provide unique keys for individuals. But when you get millions of records, as you do in a statewide database, you are going to find multiple John Jones born on the same date whose parents are Bob Jones and Sally Smith. As one probes for more information on voter registration forms, immense privacy problems emerge, and identity theft is a major societal concern. And what of the millions of citizens who are already registered to vote? Is the State going to make them register again when they've been voting for decades from the same address? I'm one of the best data architects in the business and the design of a statewide database voter registration database isn't something I'd want to do. Nor can I think of another data architect I'd trust with the task. So the states will likely put the task out on a contract to some company (Diebold comes to mind) who will promptly give it to some DBA in the United States on an H1-B visa who doesn't know enough to even design in referential integrity, let alone enforce it with unique keys, triggers, constraints, ranges, etc. Results will make it easy for anyone to vote, citizens, non-citizens, under any name, and in any precinct they can get to by getting registered as often as they can under as many names as the database has. For example I now get letters from President Bush addressed to Mr. Corry Charles, Dr. Charles Corry, and Mr. Charles Corry. Now if you can't see the problems with that you are probably an election official with an IQ on par with Adams County Clerk and Recorder Carol Snyder cited above.
As the responsibility for maintaining the database moves further from the citizen, the errors tend to multiply. Who then is responsible for detecting and correcting such errors? And if your registration is erroneous you can't vote. So all a hacker need do is create "phantom" voters or errors in the voter registration data of selected voters and control the vote in that fashion. Hackers can do their work long before the election from anywhere in the world via the Internet and the problem won't be discovered until the citizen attempts to vote, if then. At which point it will be too late to correct, or most of the electorate will be voting with a provisional ballot that probably won't be counted. Preventing a vote for your opponent is as good as a vote for your candidate or issue. Creating "phantom" voters, all of whom vote your way, is a surefire way to control an election. And these are just the tip of the iceberg for election fraud using a statewide voter registration database.
There is also an often incestuous relationship, or outright bribery between election officials and computer voting manufacturers. In any case it is clear the voting machine manufacturers tell the election officials what they want to hear rather than what they should know. But the problems with computer voting are real and the implications of the Sludge report on the flaws with Diebold software are frightening. There can be little doubt other vendors have similar flaws that they hide behind labels of "trade secret" and "proprietary software."
The statements by Rev. DeForest Soaries, former chair of the Election Assistance Commission , in the next article make it plain that our elections are ripe for fraud and theft in the wake of the Help America Vote Act (HAVA, aka Leave No Voting Company Behind).
As staff writers for the Los Angeles Times make clear in a following article, the preferred way to cheat in an election is with mailed ballots. Why then are mail ballots even used?
There is a valid reason for some absentee ballots for individuals who are in the military, will be out-of-town on election day, or are home bound and can't make it to the polls. But, increasingly, the reasons that allow voters to request an absentee ballot have been relaxed until the process is referred to as "no excuse" absentee voting. In Colorado about one third of all votes are cast by mail. In some places, e.g., areas of Washington state, as many as 85% of votes are cast by absentee ballot. And now Oregon votes entirely by mail ballot. The potential for vote fraud is radically increased by this trend, e.g., see the 2002 problems in South Dakota. In Boulder County, Colorado, it is reported that about 10-15% of all requested absentee ballots were returned by the post office as undeliverable to the address given on the absentee ballot request.
For the purported reasons of convenience, larger voter turnout, lower cost, etc. there has been a movement among election officials in several states to promote mail-in elections. The Equal Justice Foundation strongly opposes mail in balloting as the process makes a secret ballot impossible and lends itself to election fraud on many levels, some of which are documented here.
Further, the checks and balances claimed to protect the integrity and security of computer-based elections in a precinct are largely negated when the same computers are used to count mail in ballots behind closed doors. I examine a recent example of those problems in the article on the April 2003 mail in election in Colorado Springs.
I, and many other authors, examine these issues in detail in the following essays, discussions, and news reports.
Charles E. Corry, Ph.D., F.G.S.A.
| EJF Home | Where To Find Help | Join the EJF | Comments? | Get EJF newsletter |
| Vote Fraud and Election Issues Book | Table of Contents | Site Map | Index |
| Chapter 1 — Introduction To Voting Problems |
| Next — Former Election Assistance Commission Chair States There Are No Standards And System Ripe For Stealing An Election |